Identify your Information Assets
Context
The first step in the Five Step Action Plan is to identify your Information Assets.
Chances are your organisation already has an Information Asset Registry, if not, there are multiple options for defining your data.
Note that you can always come back to this step, or maintain your Information Assets directly in the Asset Registry later.
A subset of the options available to ingest the Information Asset definitions include:
- Cybersecurity Office Excel
- Assistant Recommendations
- Manual Asset Registry
Within each sub-step, click the options bar to see the available options for that sub-step.
VPDSF Preparation
If this is the first time using Cybersecurity Office, the Risk Framework, Business Impact Levels, VPDSS and other elements need to be setup. The checkboxes below will be ticked if each of the listed elements are already setup.
If there are any items that have not been checked, clicking the "Import Default VPDSF" button will load up the required data.
Note that if any of these have been customised, such as for an organisation specific Risk Framework, the associated boxes may not be ticked. If this is expected, running the import again is not required.
When setting up for the first time with the intent to deliver the PDSP, using the default import option below is recommended. Just hit the button to import all required content.
Manual Configuration
Cybersecurity Office supports the definitions of all aspects of the, which includes the Risk Framework, the Control Catalogues, Cybersecurity Frameworks, Threat Catalogue and Roadmap Horizons.
These can all be defined manually, or imported from their respective screens.
Each item is checked when the associated data is present.
Use the Import Default VPDSF button to import the default data.
Tenant Definition
Before we get into the details, we should first set the context with the details of your organisation. This will help provide context to any AI Assistant recommendations that may be used in later steps.
The Tenant Name will never be passed to AI Assistants, any references to the Tenant Name will be substituted with "The User's Organisation"
Manual Entry
Enter the details of your organisation and hit Save.
Cybersecurity Office Excel Import
The Cybersecurity Office Excel spreadsheet can also include the Platform Team definitions.
This may have been imported already along with the Information Assets in Step 1, or it can be defined or refined at this step.
You can download the current extract from here to update, and then import the changes by hitting the following button.
Assistant Recommended Profile
If your organisation is well known, or has a self-describing name, the AI Assistant can populate the profile information based on the information that you do enter, such as the name and/or summary, as a starting point.
You can then tweak or update the suggestions as required.
This is the only occasion that the Tenant Name will be sent to the AI Assistant, after you provide your consent.
You can enable and disable the Assistant via the following checkbox.
Tenant Profile
Set the name, summary and logo of your organisation as the owner of all Security Profiles associated with the current subscription.

Organisation Head
(e.g., Department Secretary, CEO)
Full Name
Position Title
Phone Number
Email Address
Postal Address
Information Security Lead
(The organisation's nominated contact the Cybersecurity Program)
Full Name
Position Title
Phone Number
Email Address
Postal Address
Which sector does the organisation operate in?
Number of employees within the organisation
Full-Time Equivalent
Contractors
Volunteers
Does the organisation have Industrial Automation and Control Systems (IACS)?
Platform Teams
These typically align with the teams, departments or organisational units that are responsible for individual systems. The Platform Team corresponds to the Owner or Custodian of System Assets.
In addition to traceability to the divisions responsible for each System Assets, this provides a means for tracking maturity and risk across the organisation.
The following options are available for the initial on-boarding of the Platform Teams.
Asset Hierarchy Holistic Entry
The Platform Teams sit at first level of the Asset Hierarchy, within which are Environments, then System Assets and Information Assets within those. Defining each level in the context of the associated entry above it can make the process more intuitive than doing each in isolation.
Manual Asset Registry Entry
Create, view, and manage the details of each Platform Team directly in the table below.
Cybersecurity Office Excel Import
The Cybersecurity Office Excel spreadsheet can also include the Platform Team definitions.
This may have been imported already along with the Information Assets in Step 1, or it can be defined or refined at this step.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Assistant Recommended Suggestions
Describe your organisation, segment and any guidance on the types of Platform Teams that should be included.
You will be presented with a number of proposed Platforms Teams to select from.
Platform Teams
System Assets
As a general rule, the value of a Systems is derived from its ability to provide access to and/or manage the Information Assets that they are responsible for.
This may be in the form of a database, an application tier system, or networking infrastructure solely responsible for transferring those Information Assets to where they need to be.
Many of the Threats from the MITRE ATT&CK® framework are based on specific types of Systems, which is used as means to identify risks to the associated Information Assets.
The following options are available for the initial on-boarding of the System Assets.
Manual Asset Registry Entry
Create, view, and manage the details of each System Asset directly in the table below.
Cybersecurity Office Excel Import
The Cybersecurity Office Excel spreadsheet can also include the System Asset definitions.
This may have been imported already along with the Information Assets in Step 1, or it can be defined or refined at this step.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Assistant Recommended Suggestions
Describe your organisation, segment and any guidance on the types of System Assets that should be included.
You will be presented with a number of proposed System Assets to select from.
System Assets
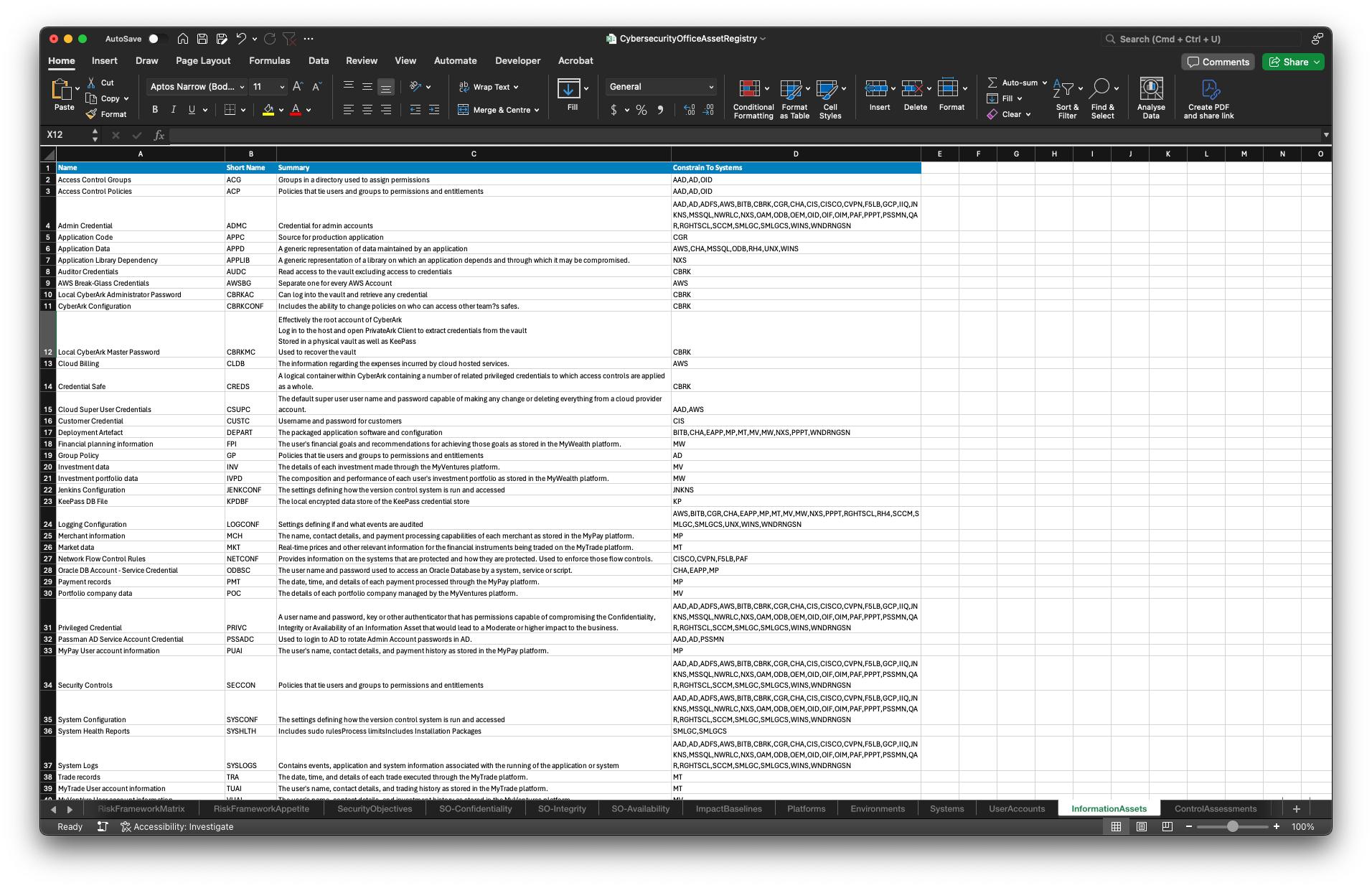
Define Information Assets
If this is the first time using Cybersecurity Office, the Risk Framework, Business Impact Levels, VPDSS and other elements need to be setup.
Manual Asset Registry Entry
Here you can create, view, and manage the details of each asset directly.
Cybersecurity Office Excel Import
One of the simplest ways to get started is to populate the Cybersecurity Office Excel spreadsheet with your data and import that.
So long as you can get your existing data into the required format, you will be able to import it all at once.
You can download the current extract from here to update, and then import the changes by hitting the following button.
Assistant Recommended Suggestions
Describe your organisation, segment and any guidance on the types of Information Assets that should be included.
You will be presented with a number of proposed Information Assets to select from.
You can repeat this process as many times as you like, so long as you stay within your AI quota.
Information Assets
Determine the 'value' of this information
Context
The value of an Information Asset is derived from the potential consequences to the organisation that may result from a compromise of that information.
In OVIC, this is referred to as the Business Impact Level, or BIL.
Consequences are typically defined as part of your Risk Framework, where the increasing level of consequences are defined across multiple categories.
Individual Victorian Public Sector (VPS) agencies may have their own Risk Framework that defines consequence levels that do not align 1:1 with the Business Impact Levels.
For example, the most critical consequence for a local Victorian council is unlikely to "cause exceptionally grave damage to the national interest", which is the most critical Business Impact Level.
Where these are not aligned 1:1, we need to map the VPS consequences to the OVIC Business Impact Levels.
Define Consequences
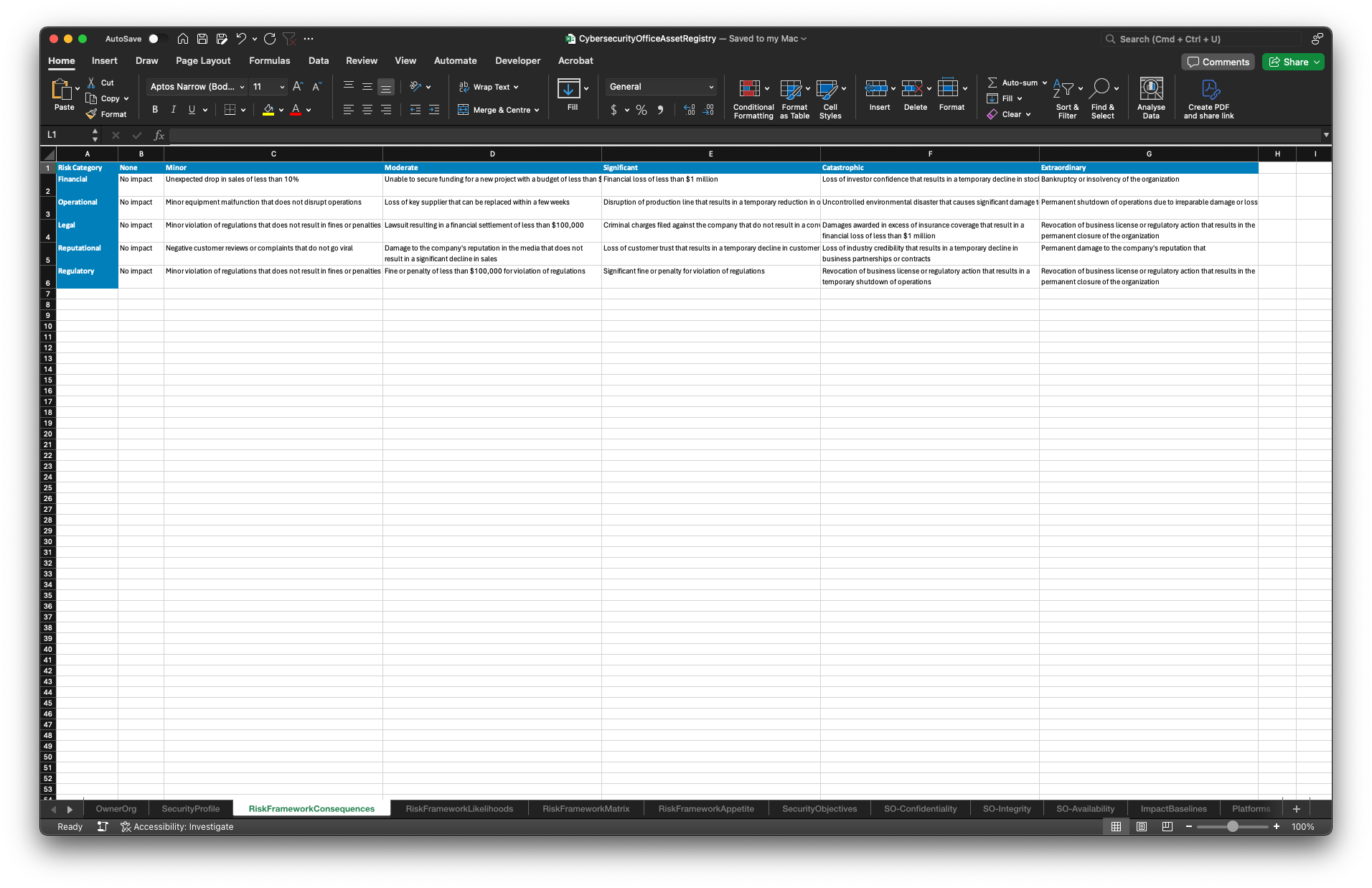
Before assessing the potential consequences arising from a compromise of your Information Assets, we first need to define the Consequences.
The following table shows the Consequence levels and their corresponding definitions across the Risk Categories.
VPDSF Business Impact Level (BIL) Default Consequences
Where a direct 1:1 mapping between the potential consequence levels for your VPS and the published VPDSF Business Impact Level definitions exists, you can simply opt to use this as the basis for your Risk Framework consequences.
This would have been imported at step 1.1, however if it has since changed or otherwise still needs to be imported, just hit the following button.
Cybersecurity Office Excel Import
The Cybersecurity Office Excel spreadsheet can also include the Risk Framework definition.
This may have been imported already along with the Information Assets in Step 1, or it can be defined or refined at this step.
You can download the current extract from here to update, and then import the changes by hitting the following button.
Consequences
Information Asset Consequences from a Compromise
Follow these steps:
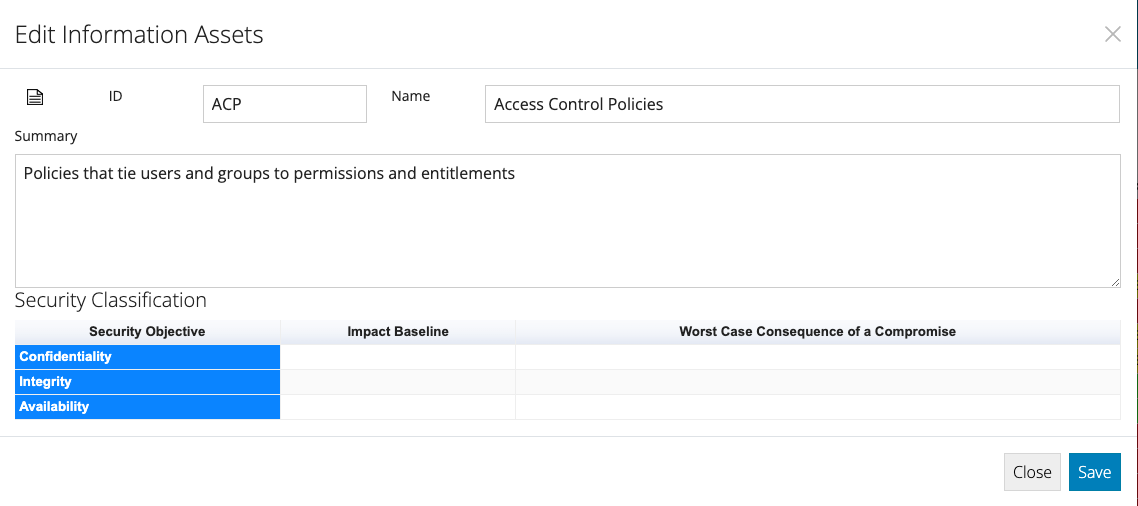
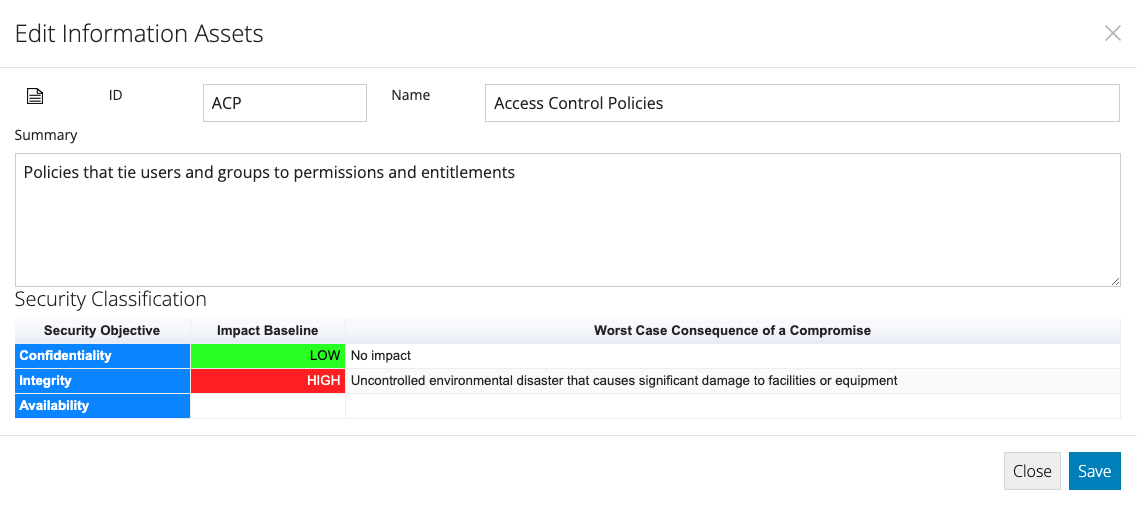
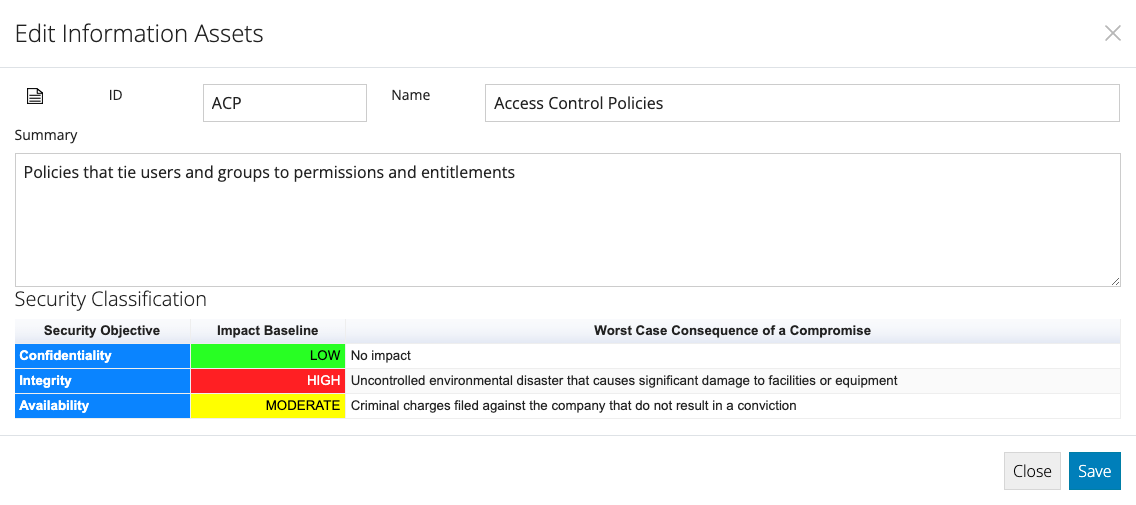
- Double click each Information Asset in the table below and refer to the Security Classification section on the dialog that appears.
-
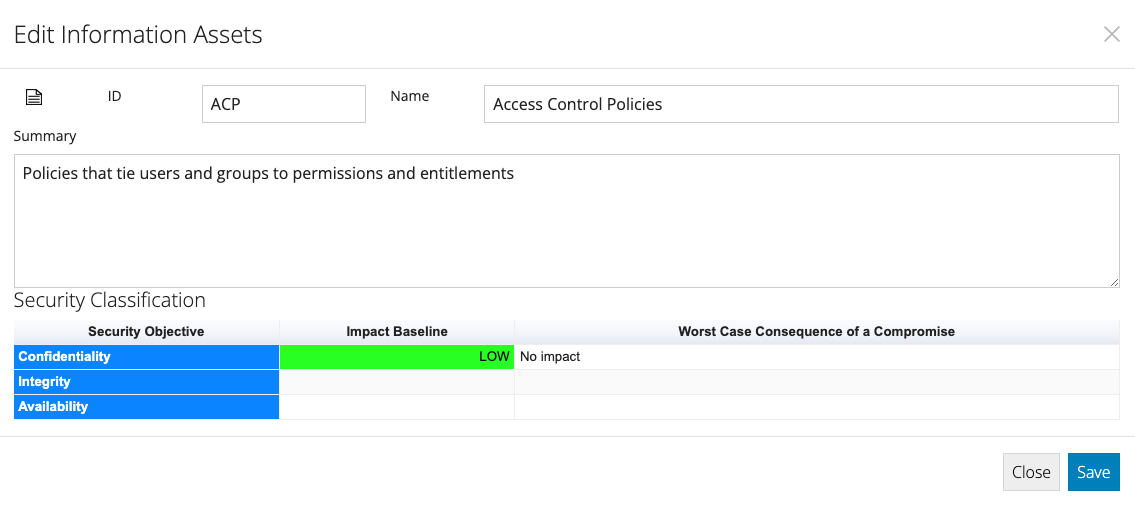
A row for the worst case consequence arising from the compromise of the Information Asset's Confidentiality, Integrity and Availability is listed.
For Confidentiality: Consider the consequences of the information being published on the internet.
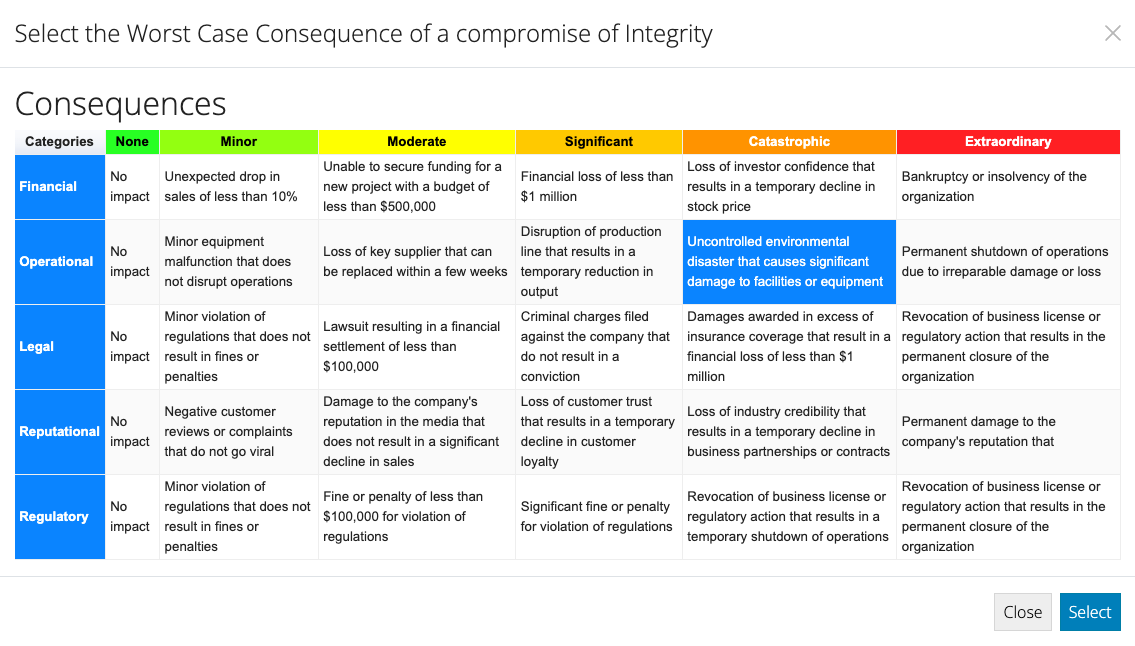
For Integrity: Consider the consequences if someone were able to change the information without authorisation.
For Availability: Consider the consequences if the information was not available when someone needs it.
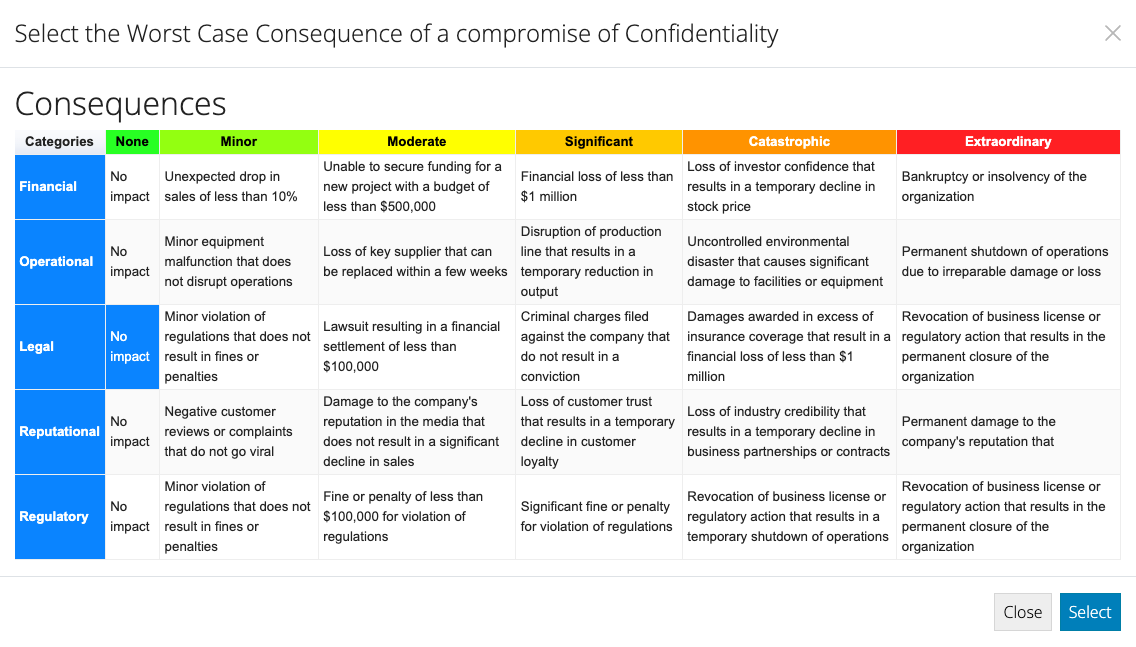
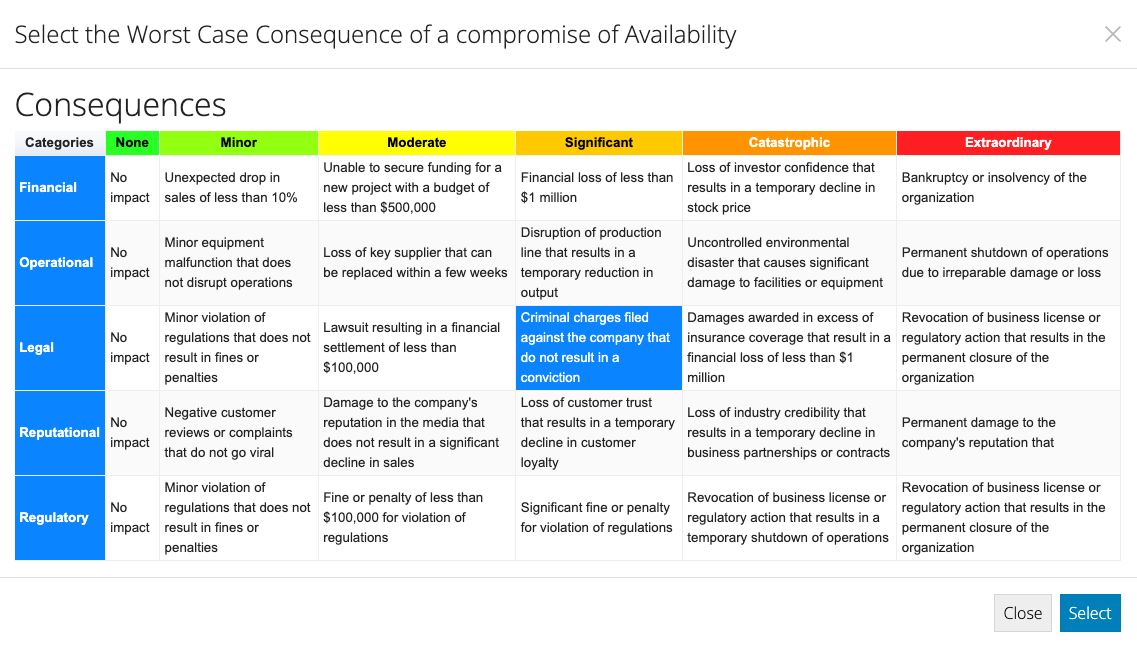
- For each of these three Security Objectives, double click the associated row and the Risk Category Consequence table will be presented.
- Start by considering which of the categories listed in the first column are likely to represent the worst case consequence in this context.
- For the category chosen, consider the description of each increasingly severe consequence from left to right in that row and click the cell that most accurately reflects the worst possible outcome from this Security Objective being compromised.
- When you are happy with the highlighted worst case consequence, hit the Select button
Manual Asset Registry Entry
Use the table below to edit each Information Asset. Double click each row in the Security Objective compromise consequences table to select the worst case compromise that may occur for each Security Objective.
Cybersecurity Office Excel Import
One of the simplest ways to get started is to populate the Cybersecurity Office Excel spreadsheet with your data and import that.
So long as you can get your existing data into the required format, you will be able to import it all at once.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Information Assets
Identify any risks to this information
Context
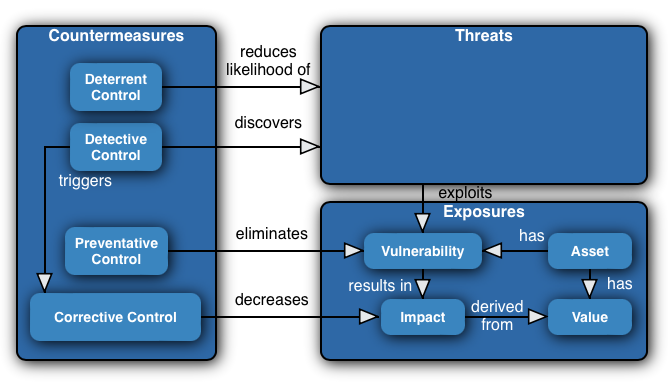
Risk = Likelihood X Consequence
To calculate the Risk, we need a few things:
- A set of potential Threats
- The Likelihood of those Threats occurring
- The resulting Consequence if they do occur
Consequence = Business Impact Level
In Step 2 we identified the potential Consequences that may arise given a compromise of each Information Asset's Security Objectives (Confidentiality, Integrity and Availability).
These consequences are mapped to the OVIC Business Impact Levels (BILs) in the Information Asset Classification Framework.
Rather than solely relying on a custom defined set of potential Threats to base the Risk assessment on, Cybersecurity Office leverages the Enterprise Techniques defined in the MITRE ATT&CK® Framework.
The MITRE ATT&CK Framework identifies a set of security controls that can be applied to reduce the Likelihood of each Threat being utilised.
Attack Vectors & VPDSS
The techniques defined in the MITRE ATT&CK Framework span technical system specific attack vectors, such as DLL Side-Loading, to broader more people and social engineering focussed techniques, such as Phishing, Supply Chain Compromise and Trusted Relationships.
The VPDSS Standards provide guidance to Victorian Public Sector organisations to extend their defence perimeter beyond just technical solutions to encompass policies, procedures, and awareness programs that mitigate risks associated with social engineering, insider threats, and external breaches.
Likelihood ∝ Control Maturity
The likelihood of a Threat occurring is inversely proportional to the Maturity of the security controls that mitigate that Threat.
Each Threat has been mapped to a set of mitigating and detective security controls in the Victorian Protective Data Security Standards (VPDSS), which all Victorian Public Sector (VPS) agencies are required to assess their security posture against.
By assessing the maturity of these controls, we can derive the potential likelihood of the Threats mitigated by those controls occurring. Combined with the consequence of the assets compromised by those threats, we have the two key factors to calculate the risk:
Risk = Control Immaturity X Business Impact Level
Asset Hierarchy
By this step we have Platform Teams, Systems Assets and Information Assets defined. We need to represent these in the Asset Hierarchy.
Manual Asset Registry Entry
You have the option of manually adding Environments for the System Assets manually by selecting each Platform Team and hitting the Add button at the bottom, or you can use the following button to simply create a single Production environment and add it to all of them automatically.
This uses a pre-defined Production Environment without leveraging the AI Assistant.
Cybersecurity Office follows the FIPS 199 and FIPS 200 approach for Information and System Asset classification. The System Asset Business Impact Level is derived from the highest Business Impact Level of the Information Assets that it is responsible for protecting.
The same 'high watermark' approach is used to roll the classifications up the Asset Hierarchy, allowing Platform Teams and the overall organisation to be classified as well.
Select the Environment within each Platform Team and hit the Add button to select each relevant System Asset. You can then select each System Asset and hit the Add button to reveal the Information Asset selection dialog. Select each of the Information Assets that the system is responsible for protecting.
Cybersecurity Office Excel Import
The Cybersecurity Office Excel spreadsheet can also include the System Asset definitions.
This may have been imported already along with the Information Assets in Step 1, or it can be defined or refined at this step.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Assistant Recommended Suggestions
You can use the following button to simply create a single Production environment and add it to all of Platform Teams automatically.
This uses a pre-defined Production Environment without leveraging the AI Assistant, however this can make setting up the Production Environment associated with every Platform Team much simpler before getting started with the Assistant.
In addition, this will prepare Control Assessments for all of the defined Controls, ready to be completed in a later step.
Populating the Asset Hierarchy requires a bit of guidance for the Assistant. You'll need to select each Environment and then use the 'Suggest Assets' button in the dropdown menu to select from the filtered results to add.
These filtered results will only include existing assets, and only those that haven't already been added to the Asset Hierarchy. The Assistant will make recommendations based on the name and description of the selected asset.
Define Threats
As outlined above, Risks in Cybersecurity Office are calculated based on the Likelihood of a Threat Occurring multiplied by the potential Consequence of it actually occurring. The Likelihood is derived from the maturity of the Controls the mitigate the Threat rather than a manual entry by a user.
The Consequences are derived from the value of the Information Assets that the Threat could lead to the compromise of.
Therefore, Risks need to be entered as Threats associated with mitigating Controls.
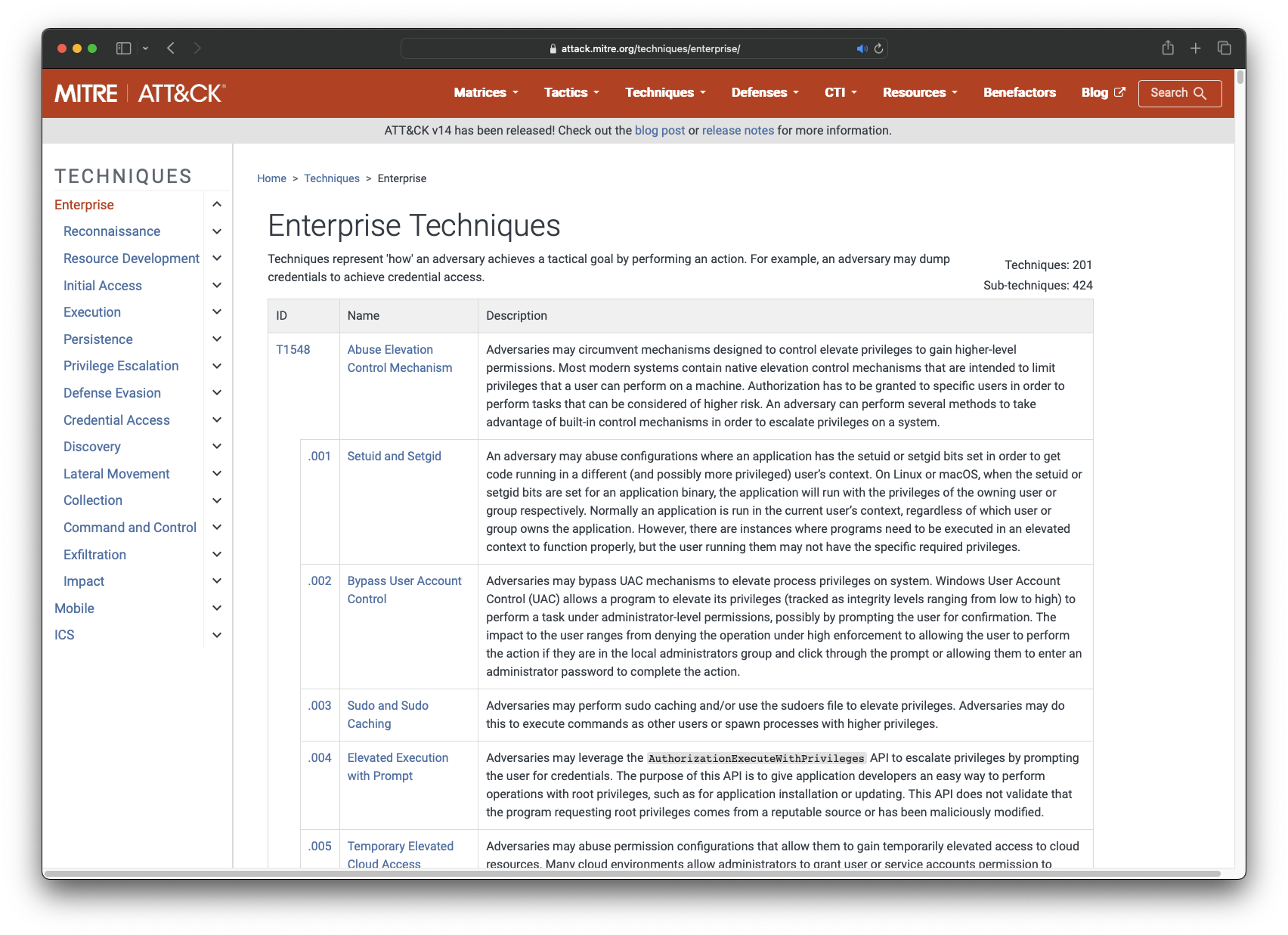
MITRE ATT&CK® Enterprise Techniques
Regardless of whether there are specific Risks that need to be recorded, it is highly recommended that the MITRE ATT&CK Enterprise Techniques are used to broadly identify potential threats to the VPO agency's Information Assets.
Using the MITRE ATT&CKEnterprise Techniques does not preclude the manual entry of custom Risks.
Manual Threat Registry Entry
Create, view, and manage the details of each Threat directly in the table below. Ensure that any Threats defined have one or more associated mitigating Controls selected from the VPDSF to ensure they are incorporated in the assessment.
Cybersecurity Office Excel Import
The Cybersecurity Office Excel spreadsheet can also include the System Asset definitions.
This may have been imported already along with the Information Assets in Step 1, or it can be defined or refined at this step.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Threats
Control Assessment
The Asset Hierarchy is derived from the Platform Teams, Environments, System Assets and the Information Assets protected by them.
We start the assessment at the root of the Asset Hierarchy, identifying the Control Objectives that have been met for each security control across the organisation.
The objective is to provide the answers that will have the fewest exceptions.
Then, on a Platform Team by Team basis, we ask whether the assessment performed at the root of the hierarchy applies to all of their systems, and override any control assessments that differ.
This gives us a broad organisation-wide assessment, as well as a nuanced assessment on a team-by-team or system-by-system basis, or any combination of the two.
A few tips:
- Every element of every table can be double clicked to bring up more information on each one. This includes double-clicking individual Control Assessments in the bottom left panel to see the description of the associated Control.
- You can perform a Bulk Assessment of all or a subset of Controls by cliking the split-button triangle to the right of the "Create" button below the Control Assessments table and clicking the "Bulk Assessment" menu item. This allows you to set a broad maturity level first, and then tweak it on a per Control basis.
Manual Asset Registry Entry
Here you can create, view, and manage the details of each asset directly.
Cybersecurity Office Excel Import
One of the simplest ways to get started is to populate the Cybersecurity Office Excel spreadsheet with your data and import that.
So long as you can get your existing data into the required format, you will be able to import it all at once.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Security Profile Assets
Metrics
Control Assessments
State
Apply security measures to protect the information
Context
Target Control Objectives
In Step 3, we identified the Control Objectives that have been met in the current state of the environment. These Control Objectives correspond to the different maturity levels of the VPDSS Elements.
VPDSF Capability Maturity Model
The Victorian Protective Data Security Framework (VPDSF) defines 5 levels of maturity.
| Maturity Level | Summary |
|---|---|
| Informal | The organization has irregular, undocumented processes with improvements being reactive and dependent on individual expertise. There is a risk of capability loss if key staff leave. |
| Basic | Security is valued with clear responsibilities assigned. Basic security measures are implemented and monitored, leading to more consistency, especially within individual units. Policies are documented, but processes might not be. Security risks are reviewed occasionally, and significant issues are addressed. |
| Core | Policies, processes, and standards are clearly defined and uniformly followed throughout the organisation. Effective governance and management structures exist. Risk assessments are regularly conducted and historical performance data is used to identify improvement areas. |
| Managed | Activities adapt dynamically to situational changes. Quantitative measures are used for objective security performance analysis and prediction. Beyond basic requirements, the organisation also adopts many optional best practices based on risk assessment. |
| Optimised | Security is a strategic issue for the organisation. Long-term planning is in place and integrated with business planning to predict and prepare for protective security challenges. Effective continuous process improvement is operating, supported by real-time, metrics-based performance data. Mechanisms are also in place to encourage, develop and test innovations. |
'Core' is the default target maturity level in Cybersecurity Office, however this can be set to any level. Cybersecurity Office will derive all of your required Control Objectives to be introduced to meet this target maturity level.
These derived targets can also be overridden.
Security Program Roadmap
Cybersecurity Office automatically performs a gap analysis between the current state and target state to identify the Control Objectives that need to be introduced in order to reach the defined target maturity level.
Next we need a set of Tasks that will realise these concrete set of Control Objectives that need to be introduced. For each introduced Control Objective, one or more Tasks need to be defined.
Finally, the Tasks are grouped together into Work Packages, which are roughly analogous to projects. These are presented on a roadmap, prioritised based on dependencies and ROI derived from the Tasks they contain. The ROI is derived by the 't-shirt sized' cost and benefit associated with each.
As Tasks are completed, their associated target Control Objectives are realised, which corresponds to a maturity level increase for the associated control, which decreases the Likelihood of any associated Risks.
In short; as maturity increases, risk decreases.
Protective Data Security Plan (PDSP)
The PDSP document needs to be prepared by each Victorian Public Sector (VPS) agency on a biennial basis. It provides a means to identify the risks, status, maturity and timeframes associated with each VPDSS Element completion at an organisation-wide level.
The maturity assessment for each VPDSS Standard identifies the current state maturity level, a two year horizon target and a horizon target, which correspond to the Horizons on the Roadmap in Cybersecurity Office.
This document can be populated almost entirely by Cybersecurity Office.
Target State
There are four remaining steps required to prepare for the PDSP.
- Confirm target maturity level
- Review, confirm/revise target Control Objectives
- Define the Tasks to realise the introduced Control Objectives
- Group the Tasks into Work Packages
- Populate the PDSP
Confirm Target Maturity Level
By default, the target VPDSF maturity level is 'Core'.
This can be changed by double clicking the desired maturity level and checking the 'Target' box.
Manual Maturity Model Entry
New Maturity Models can be created and existing ones edited using the table below. Double click existing entries to edit or use the buttons to create or delete new ones.
Cybersecurity Office Excel Import
One of the simplest ways to get started is to populate the Cybersecurity Office Excel spreadsheet with your data and import that.
So long as you can get your existing data into the required format, you will be able to import it all at once.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Maturity Models
| Name | Summary | Is Default |
|---|
Review, Confirm/Revise Target Control Objectives
As per the current state assessment of the VPDSS controls, the target state can be defined hierarchically as well.
Start at the root of the asset hierarchy, select each Control Assessment and reveal the Gap Analysis tab.
A tick in the 'Derived' column of the Control Assessments table indicates that the target maturity level for this control, and the associated Control Objectives were determined automatically. These are selected based on the following criteria:
- The Control Objective is at or exceeds the target maturity level and is already met in the current state
- The Control Objective is required to meet the target maturity level
- The Risk Appetite defined in the Risk Framework requires a higher maturity level for this control to bring the associated risk to within the acceptable risk threshold
You have the option of leaving the derived target state as it is, or you can individually select or deselect any Control Objectives and save the target state control assessment to manually defined the level required. This can be done across the entire organisation at the root of the asset hierarchy, or on a Platform Team, environment or system specific basis.
Use the Notes tab to optionally record any additional commentary around the implementation of this VPDSS control element. These Notes will be aggregated into the associated field for the associated VPDSS Standard in the PDSP.
Manual Asset Registry Entry
Use the table below to edit each Information Asset. Double click each row in the Security Objective compromise consequences table to select the worst case compromise that may occur for each Security Objective.
Cybersecurity Office Excel Import
One of the simplest ways to get started is to populate the Cybersecurity Office Excel spreadsheet with your data and import that.
So long as you can get your existing data into the required format, you will be able to import it all at once.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Security Profile Assets
Metrics
Control Assessments
State
Tasks to Realise Control Objectives
For each Control Objective that needs to be introduced, use the Add or Suggest Task option. Introducing a Control Objective may require multiple Tasks with dependencies between them. The Task associated with the Control Objective is the one that, once it and its dependencies have been completed, will mean that the Control Objective has been realised.
If there are any team, environment or system specific Tasks required, you can expand the asset hierarchy and select the relevant Asset Group or System Asset and define more nuanced Tasks.
Note that the dependencies between Tasks must not have any cyclic dependencies in them.
Manual Task Entry
To define tasks at the organisation level, select the Security Profile at the root of the asset hierarchy. Then select each Control Assessment to see the Control Objectives that need to be introduced in the Target State. Add or Create Tasks for each.
Cybersecurity Office Excel Import
One of the simplest ways to get started is to populate the Cybersecurity Office Excel spreadsheet with your data and import that.
So long as you can get your existing data into the required format, you will be able to import it all at once.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Security Profile Assets
Metrics
Control Assessments
State
Group the Tasks into Work Packages
The Tasks need to be grouped together to allow a more coarse-grained management of the units of work. Related Tasks that have similar Cost and Benefit should be grouped together such that the resulting Work Package can be prioritised accordingly.
Each Work Package should only be considered completed when all Tasks within the Work Package are completed, meaning that there is a correlation between the completion of any given Work Package and an associated increase in maturity and decrease in risk.
Note that the dependencies between Work Packages must not have any cyclic dependencies in them. These dependencies are derived from the dependencies between the Tasks they contain.
Manual Work Package Entry
Work Packages are just groupings of related Tasks. Use the Create button to start a new Work Package. From within the Work Package dialog, add Tasks via the Task selection dialog.
Cybersecurity Office Excel Import
One of the simplest ways to get started is to populate the Cybersecurity Office Excel spreadsheet with your data and import that.
So long as you can get your existing data into the required format, you will be able to import it all at once.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Assistant Recommended Suggestions
The Assistant can assess the set of unpackaged Tasks, identify those that are related and make recommendations for new Work Packages containing them.
This may require multiple requests to the Assistant to package all Tasks as this is an complex request.
Horizons
Work Packages
Content for tab 3.
Populate the Protective Data Security Plan (PDSP)
Once Steps 1 to 3, and Steps 4.1 to 4.4 have been completed, most of the details required to populate the PDSP are in the system.
A few additional details are required to complete the Agency Head Executive Summary.
- First, create the PDSP report by clicking the Create button below.
- Give it a name, such as PDSP 2024 and a summary. This information is not included in the generated PDSP, but helps distinguish different reports in the system.
- Click the Save button.
- Double click the newly created report to open it.
- You can browse the information already populated in the report by clicking to expand each section (Part A, B and C).
- To complete the report, click the Edit button.
- The first screen shows the details provided at report creation time. If no changes are required, click the next arrow button, otherwise enter the updated information and click the Save button.
- The first time you reach Step 2, the system may need to generate all of the standard sections, which can take a while. Wait until you see all 12 standards listed.
-
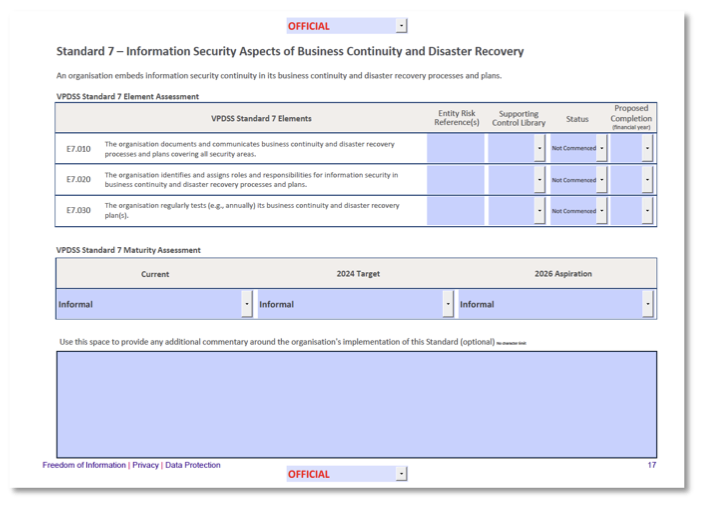
Step through each standard. The majority of the content for each standard is pre-populated for you.
You only need to provide some commentary, however you can use the "Suggest Commentary" menu item in the split button sub-menu by clicking the triangle to the right of the "Save" button.
This will prompt the Assistant to generate the commentary based on the current and target state standards, tasks and Work Packages. Use the suggested commentary as a starting point to adapt your own thoughts.
- In step 3.1, enter all of the required information. Much of it will be pre-populated based on informatin provided earlier. The commentary needs to be provided manually as it is based on activities that occurred in the past.
- In step 3.2, check the boxes against any of the issues encountered and provide commentary regarding these in the text field.
-
In step 3.3, the most complex part of this section is pre-populated and derived from the information asset classication performed earlier.
These can not be overridden without going back and updating the classifications at an earlier step and then refreshing this section (See the split-button sub-menu at the bottom of the page to refresh).
Check the boxes and enter the values in the other editable fields. In the Generative Artificial Intelligence sections, if you used any of the AI Assistant suggestion features in the app, the types of information used as inputs into LLMs include system and information asset registry details, security controls and their maturity and securiy program planning information.
- In step 4, enter the details of the person responsible for signing off on the PDSP. Note that the 'insert signature here' box is a placeholder. This will be signed either by printing out the generated PDF, signing and scannign it, or via digital signature within Adobe Acrobat or other PDF editing software.
- Lastly, click the "next" arrow button to return to the main PDSP Report screen and click the "Download Report" button. Review the resulting document, make any adjustments within the app if required, regenerate the PDF and repeat until the desired outcome is achieved.
An online version of the report is available below, with the areas requiring additional entry highlighted.
This empty OVIC report template can be downloaded in the 2024 PDF template format, or the content can be copied over to the latest PDF template if required.
Manual Report Entry
Use the table below to create a new PDSP report and then populate it. Most of the content reflects the current state of the assessment and can not be edited without going back to the relevant section an updating the assets or their assessments. The commentary and externally sourced information needs to be entered.
Cybersecurity Office Excel Import
One of the simplest ways to get started is to populate the Cybersecurity Office Excel spreadsheet with your data and import that.
So long as you can get your existing data into the required format, you will be able to import it all at once.
You can download the current extract from here to update, and then import the changes by hitting the following button.

Manage risks across the information lifecycle
Continuous Improvement
Step 5 does not involve producing any new deliverables, but instead entails revisiting Steps 1 through 4 on a regular basis.
As a centrally maintained enterprise SaaS solution rather than a point in time document based deliverable, Continuous Improvement is an inherent capability.
Individual parts of the assessment can be maintained by the teams responsible for those controls, or outsourced to third-parties for an independent review.
In all cases the results will be consistent and the IP retained.
| Step 5 Deliverable | Reference |
|---|---|
| Reassess the value of Information Assets at least annually | Revisit Step 1.5 and/or Step 2.2 to retire any old Information Assets, introduce new ones and update existing definition and the associated consequences of a compromise for each one. |
| Update the Information Asset Registry | This is inherently completed as part of reassessing the value of the Information Assets above. |
| Update Risk Registers | Revisit Step 3.2. New 'Current State' snapshots can be defined at any time, allowing progress between re-assessments to be tracked over time in addition to forecast projections. |
| Updates the PDSP as required | Revisit Step 4 |
| Notify OVIC of any Information Security Incidents | This is not currently supported within Cybersecurity Office. Refer to the OVIC Information Security Incident Notification Scheme |